Sie zeigen eine alte Version dieser Seite an. Zeigen Sie die aktuelle Version an.
Unterschiede anzeigen
Seitenhistorie anzeigen
Version 2
Aktuelle »
Description:
This document describes the procedures for linking XAUTH to an external RADIUS server when operating LCOS 7.80. By linking XAUTH to RADIUS servers, you can control VPN client access on a per-user basis with central user administration, and you can use OTP tokens.
Requirements:
The following scenario assumes that a configured VPN dial-up connection without the XAUTH extension is already available.
Scenario:
A laptop with installed Advanced VPN Client (AVC) is to have access to the LAN at the main office via a VPN connection. Because the laptop is used by different employees with their own access data, it must be possible for each employee to enter his or her credentials when establishing the VPN connection. The access data of the employees are stored on a RADIUS server at the main office. The data are maintained here and/or replicated with the Active Directory user accounts of the central Windows 2008 Server (single-sign-on).
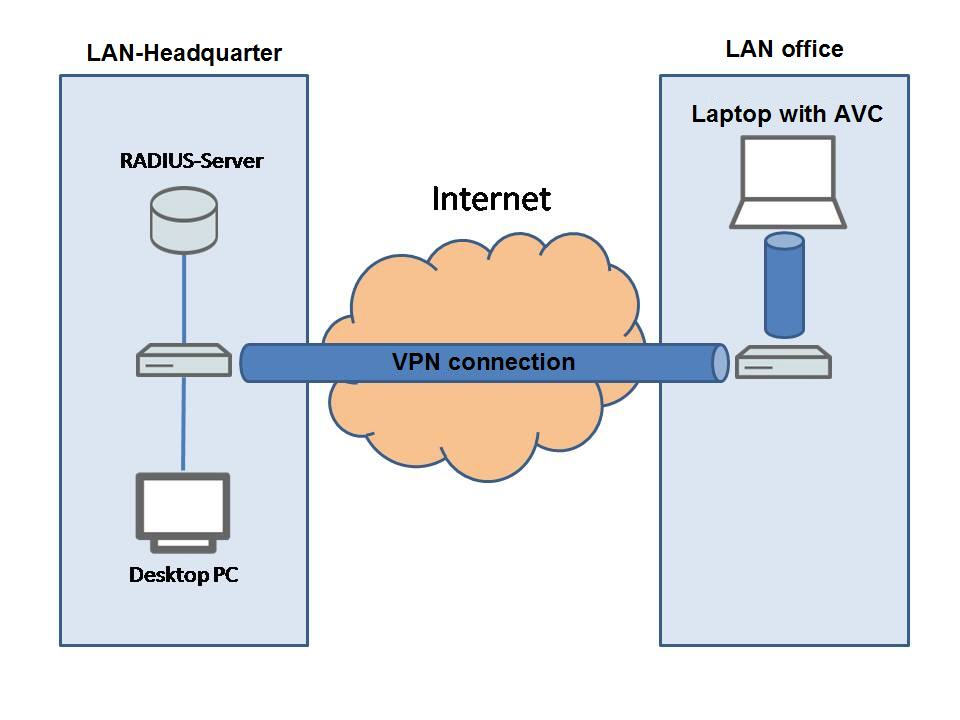
Converting the existing VPN dial-up connection to the authentication via XAUTH and an external RADIUS server consists of two parts.
Part 1 (LANCOM router):
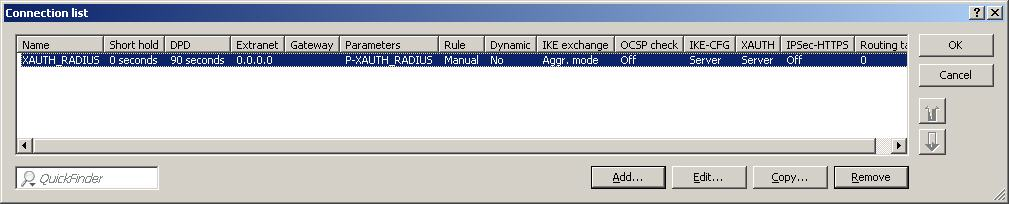
Navigate to Configure -> VPN -> General and, for the appropriate entry in the connection list, set the switch for XAUTH certification to "server". This enables the router to use the XAUTH extension for the example connection "XAUTH_RADIUS".
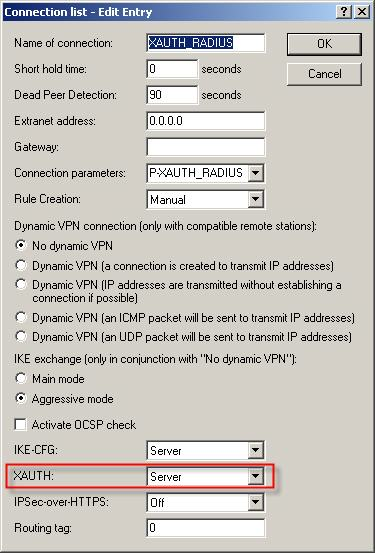
For the IKE keys and identities under Configure -> VPN -> IKE auth., the local identity type and the remote identity type must be set to Key ID (group name) for the appropriate connection. Identities which have been assigned already and the preshared key remain unchanged.
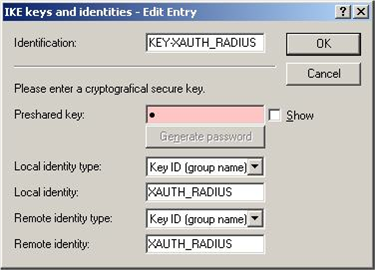
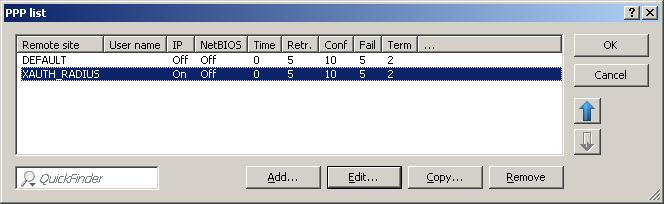
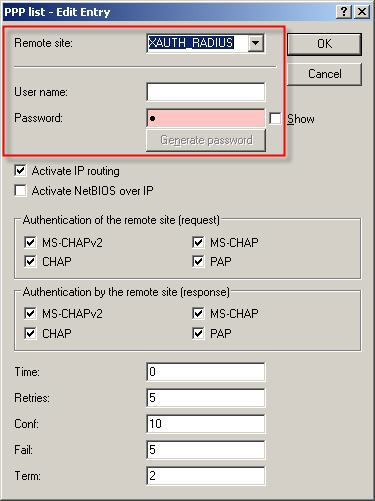
To enable XAUTH to query the user name and/or password, a new entry must be added to the PPP list under Configure -> Communication-> Protocols. As the name of the remote site, the relevant VPN connection is selected from the drop-down menu in the connections list. A user name is not explicitly defined here. The password which is entered here should be as complex as possible to prevent the unauthorized use of the Advanced VPN Client. Finally, IP routing is to be activated.
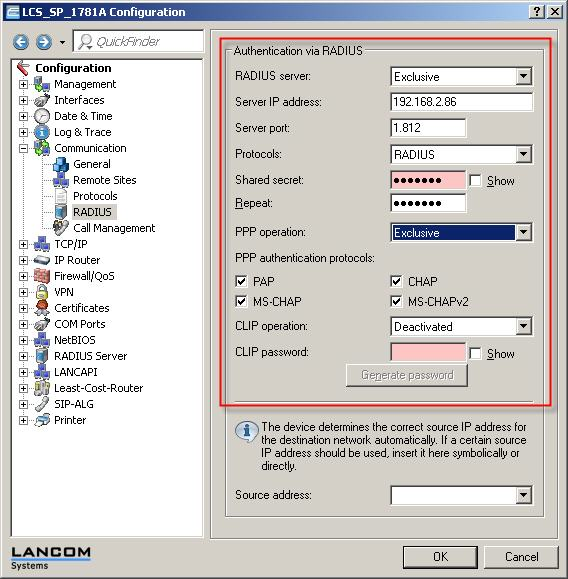
The connection to the external RADIUS server is configured under Configure -> Communication -> RADIUS. The following settings are required:
- RADIUS server: Set to Exclusive
- Server IP address: Enter the IP address of the external RADIUS server
- Server port: Set the external RADIUS server communications port (default 1812)
- Protocols: Set to RADIUS
- Shared secret: Enter the shared secret that is configured on the external RADIUS server.
- PPP operation: Set to Exclusive
All other settings can remain as their default values.
This completes the preparation of the router.
Part 2 (Advanced VPN Client):
In AVC, too, only the existing profile is modified. To do this, select the profile which applies to the connection.
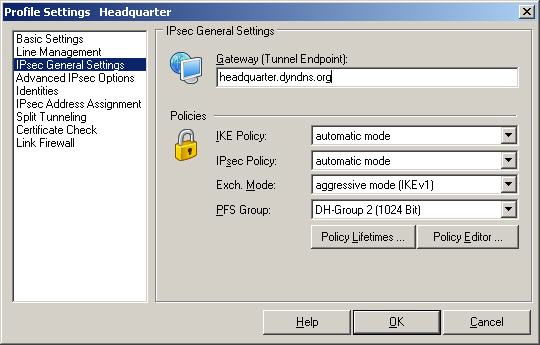
Under the menu item "Identities", the local identity type is set to "Free string used to identify groups". Also, a check mark is set for "Extended Authentication" (XAUTH extension).
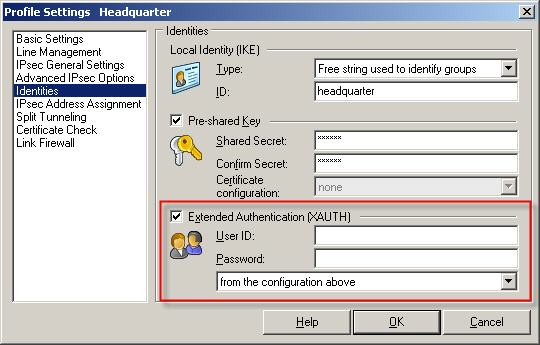
If the user name and/or password are not entered here, then AVC will request the user for the missing data before establishing IPSec phase 2.
Supplementary information:
XAUTH does not increase the security of the VPN connection itself. However, this extension prevents unauthorized access to the company network by means of unprotected or password-cracked devices. Password protection under Windows is relatively weak. Even if you can get around the user password, there is not yet a connection to the company network.
|
|
|