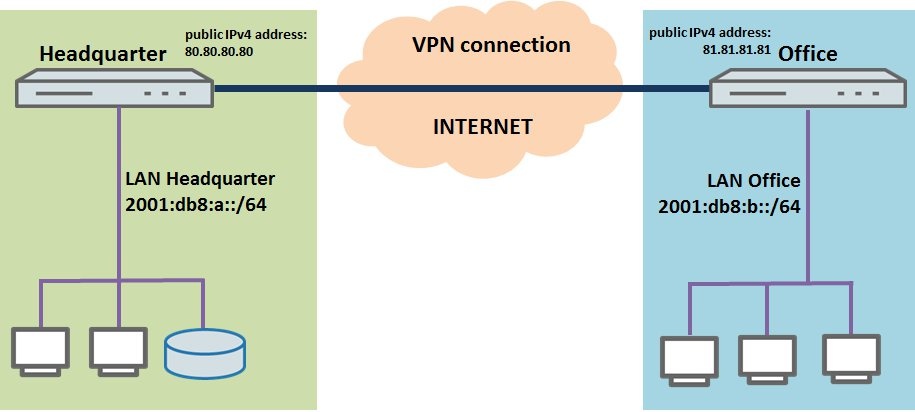
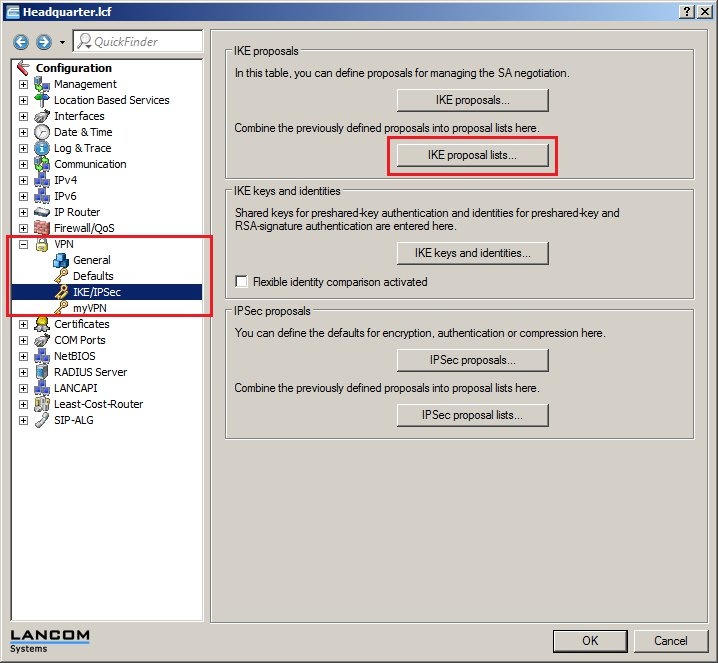
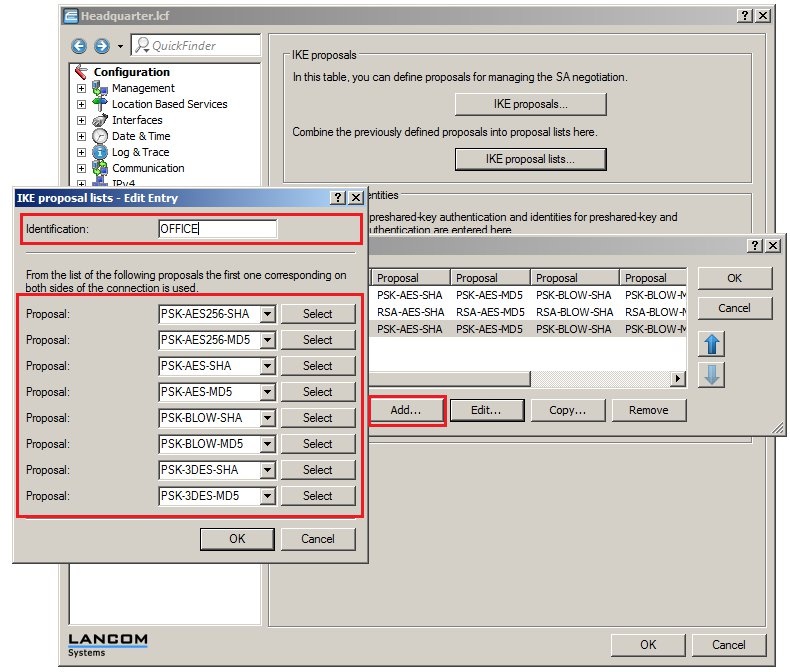
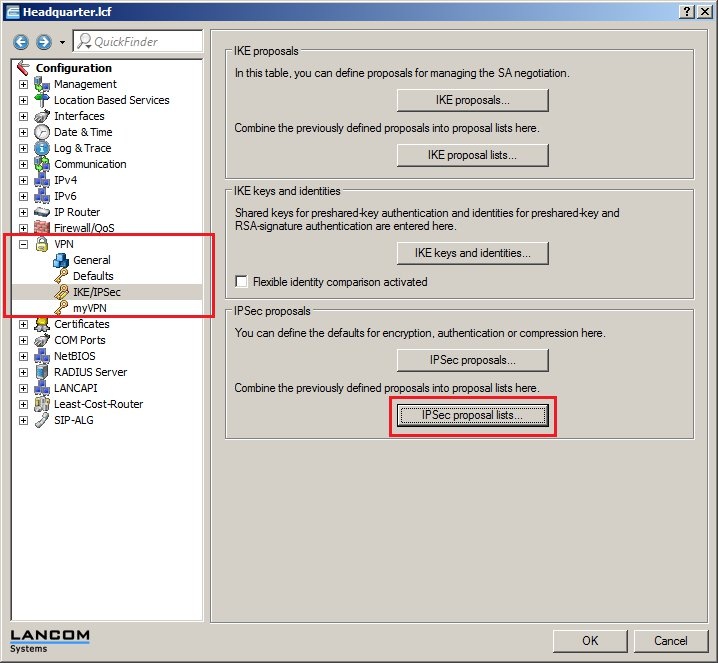
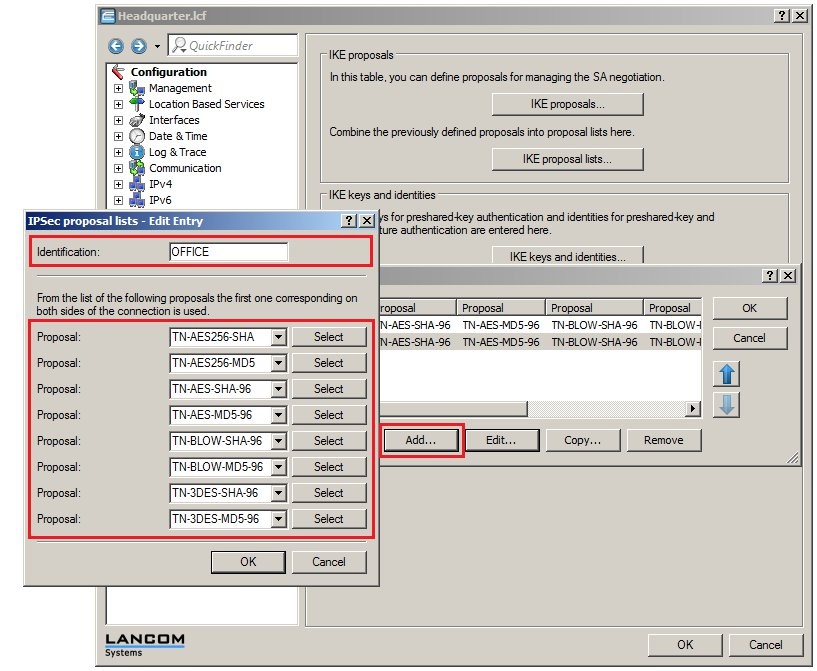
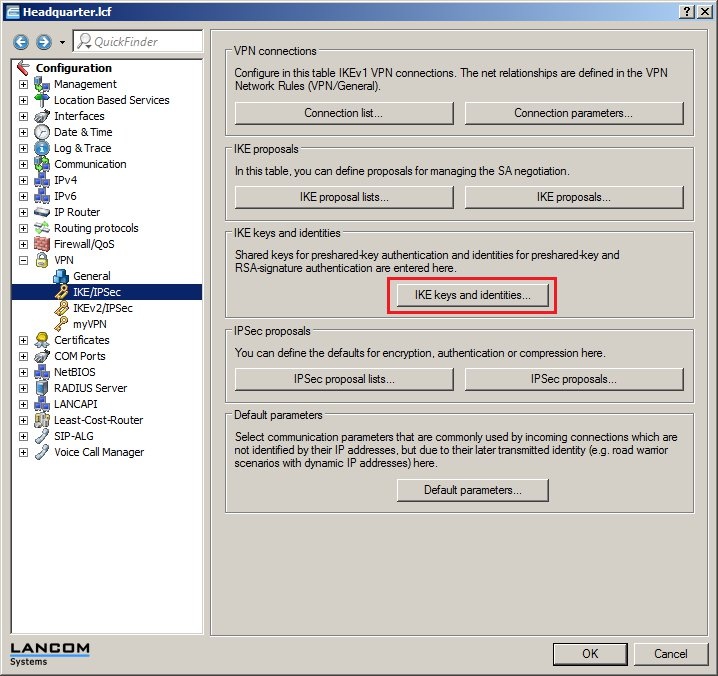
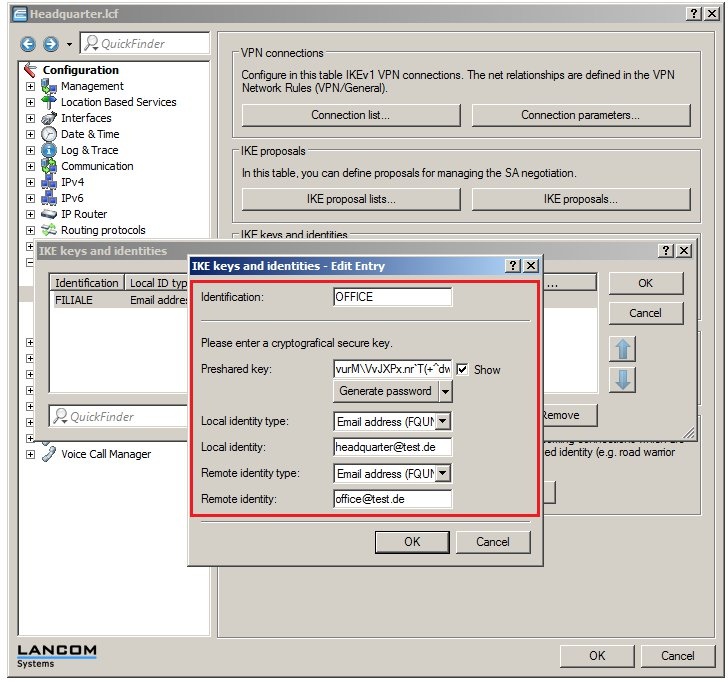
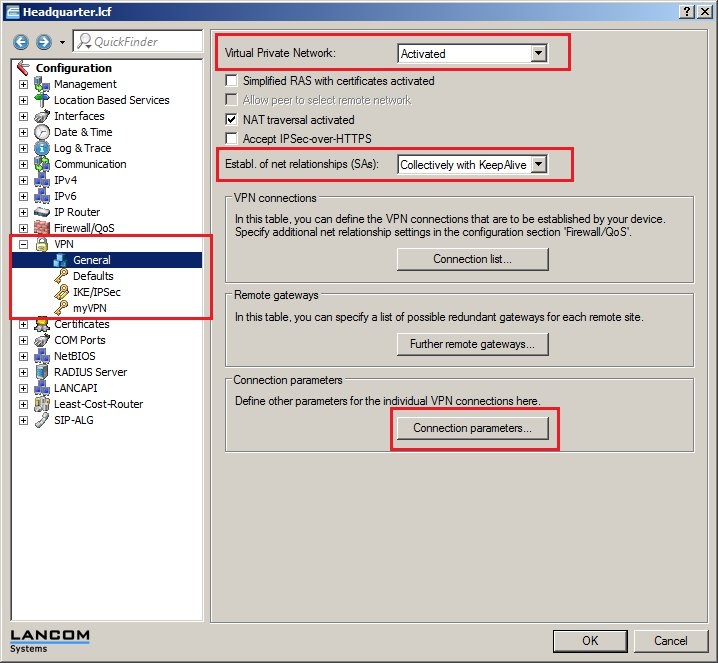
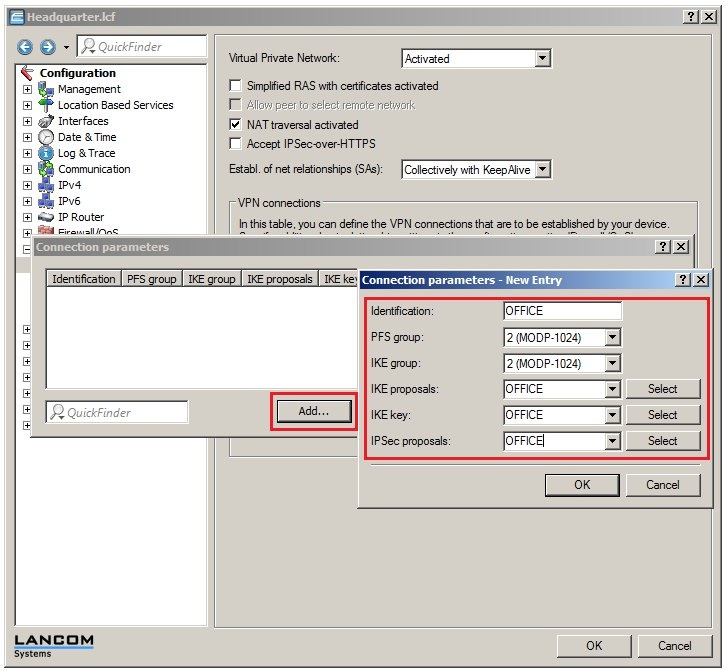
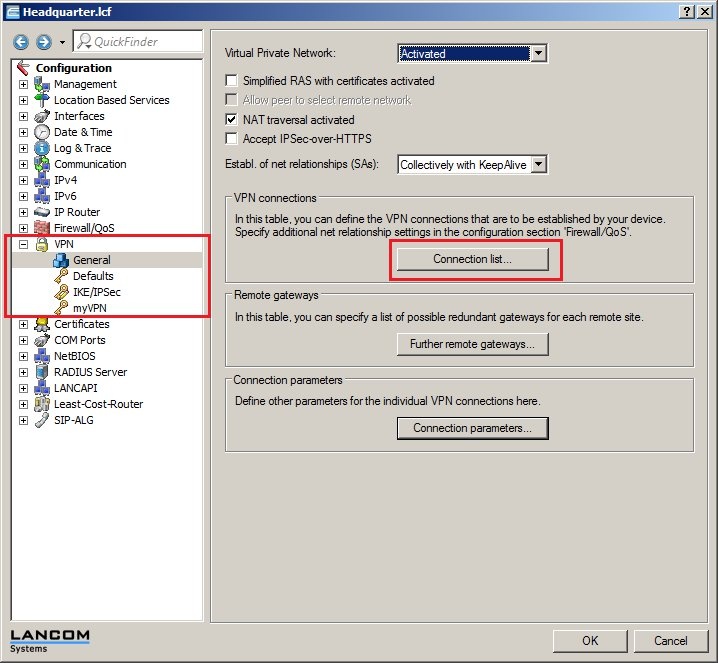
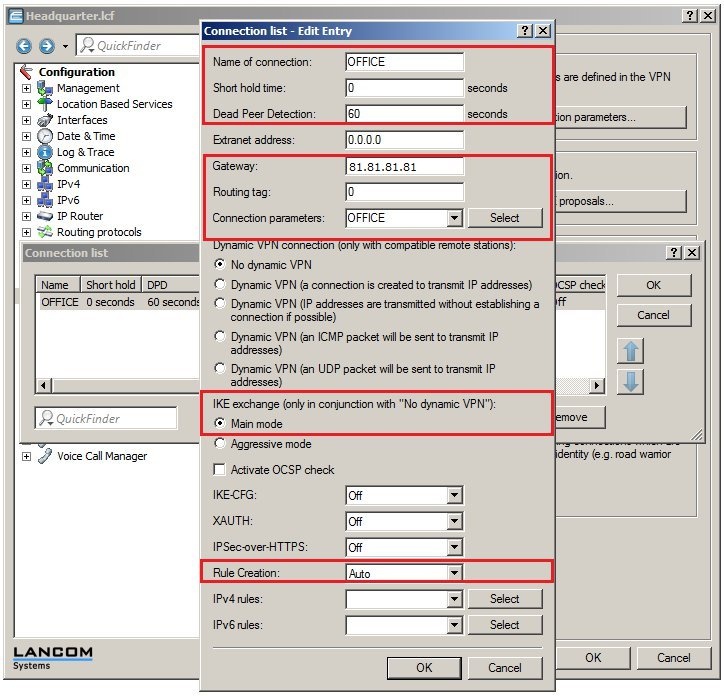
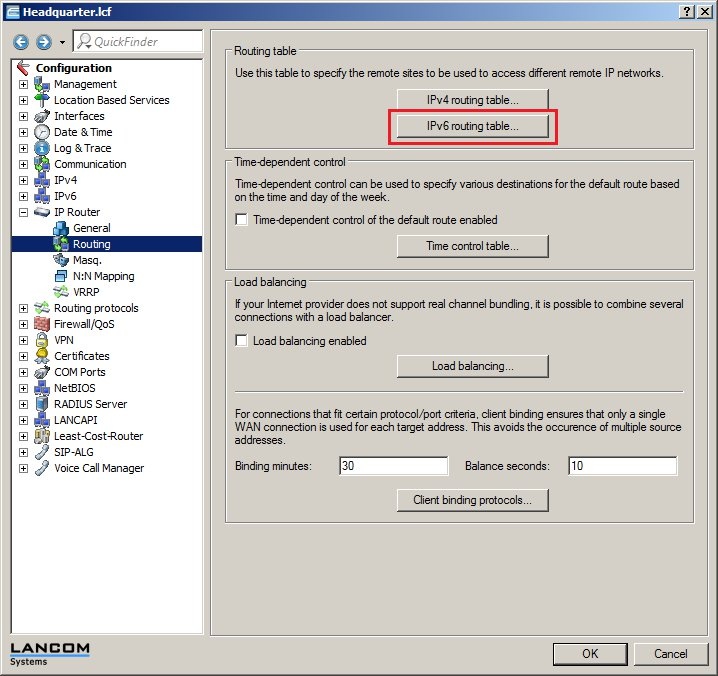
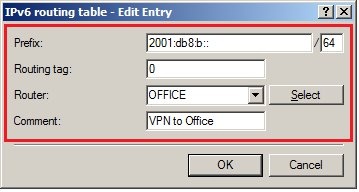
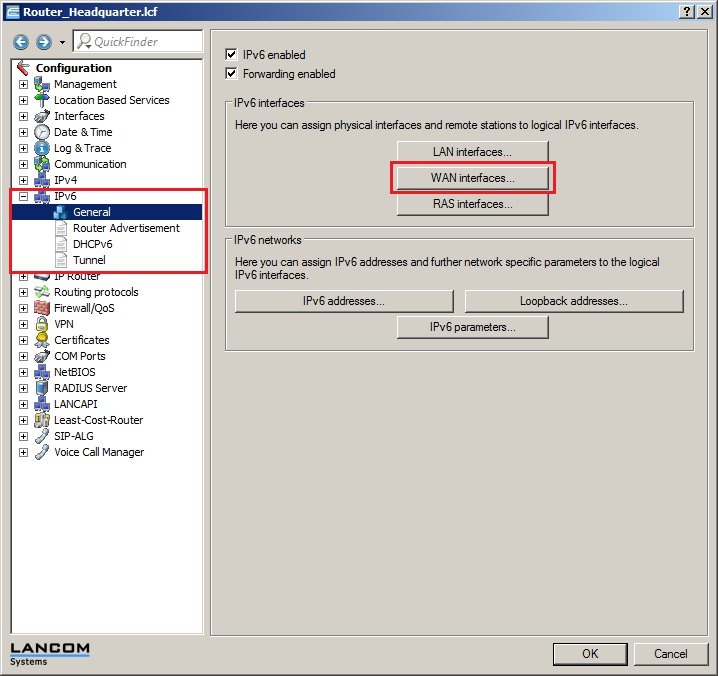
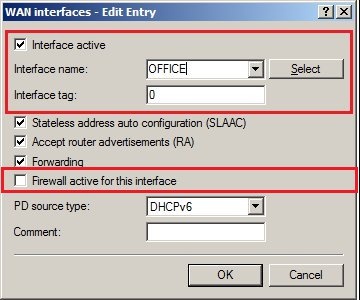
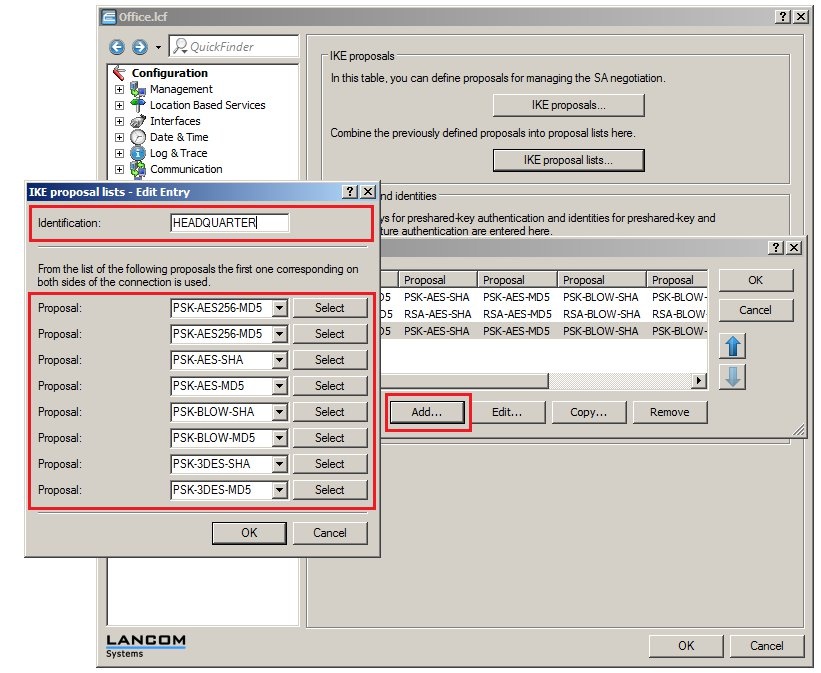
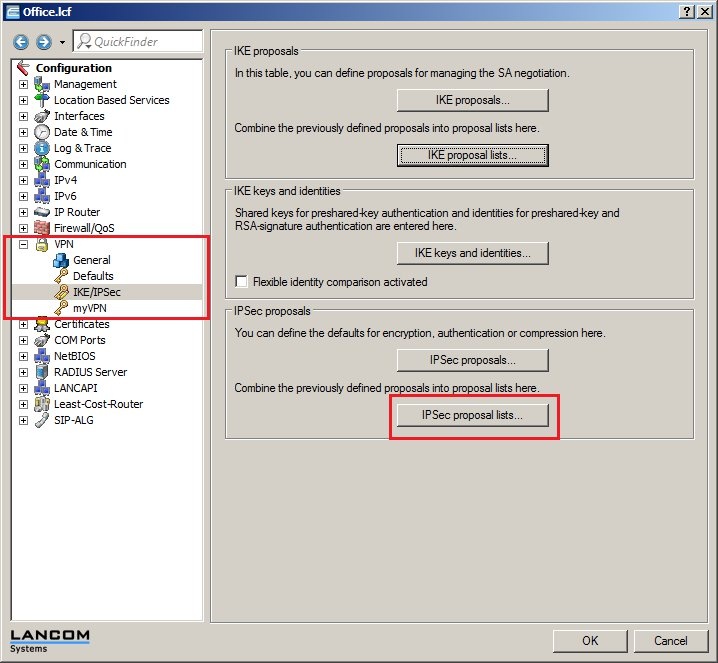
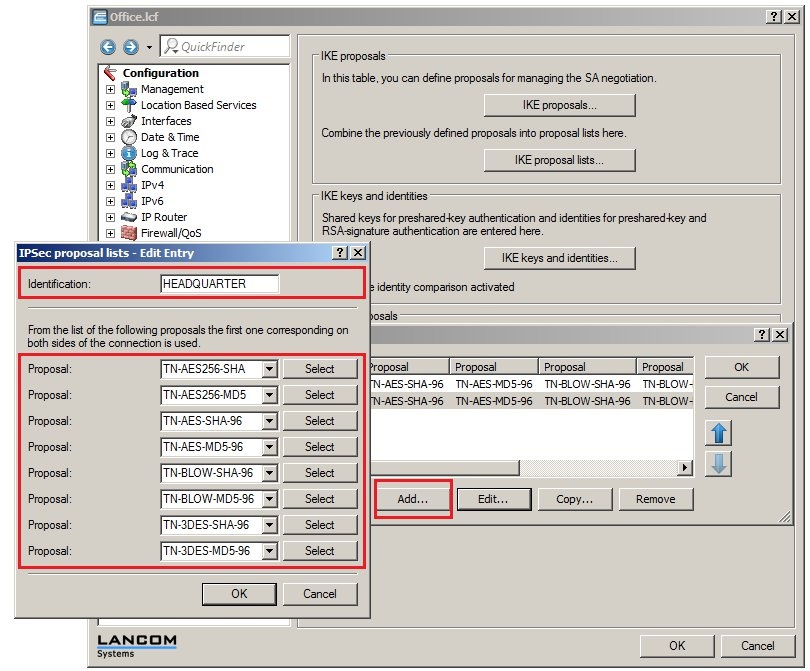
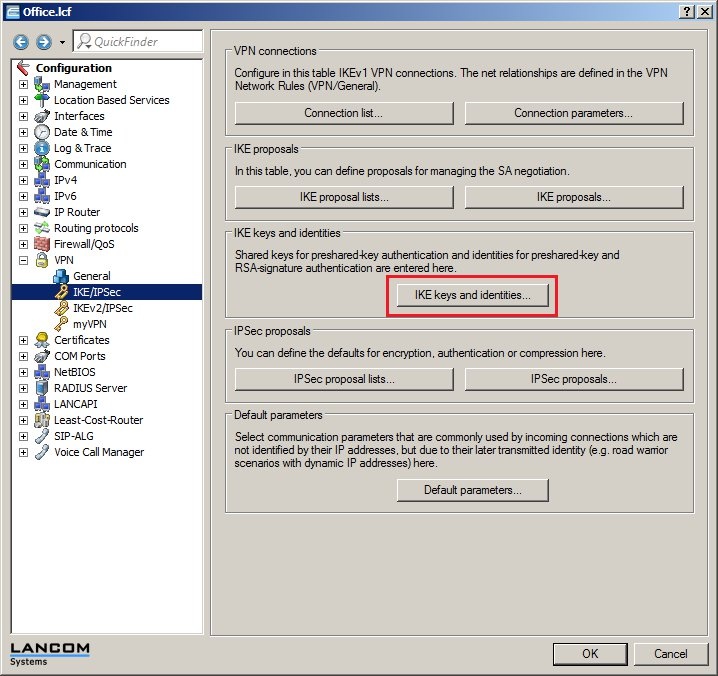
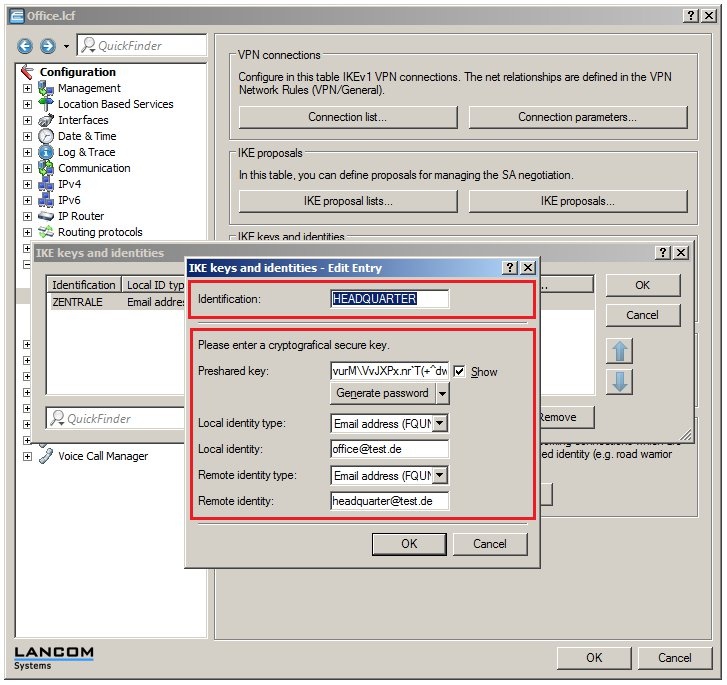
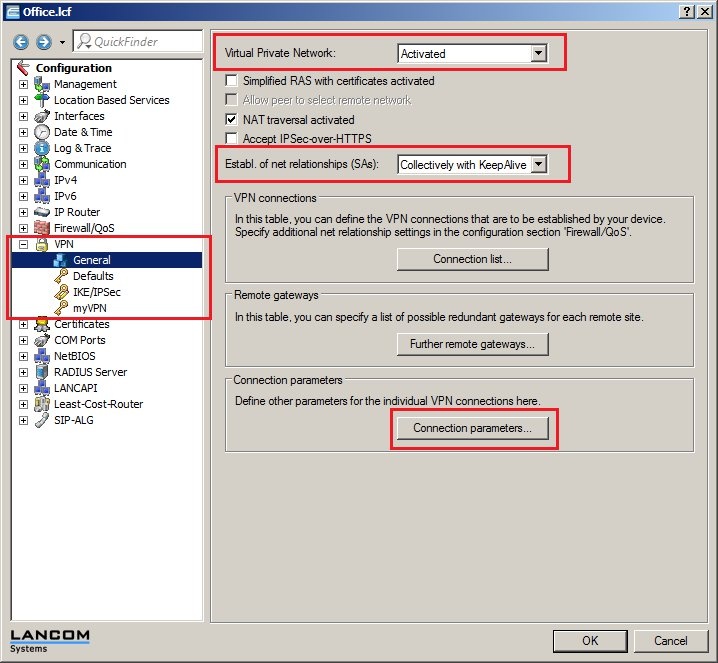
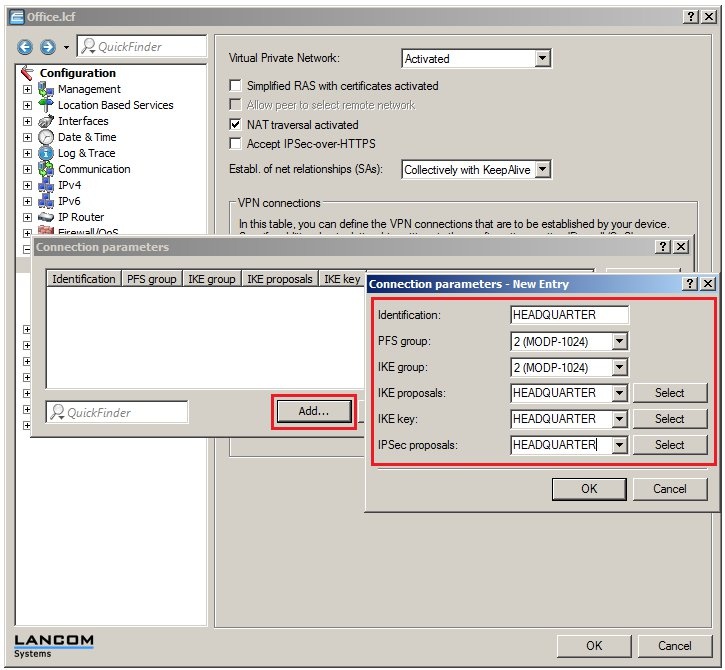
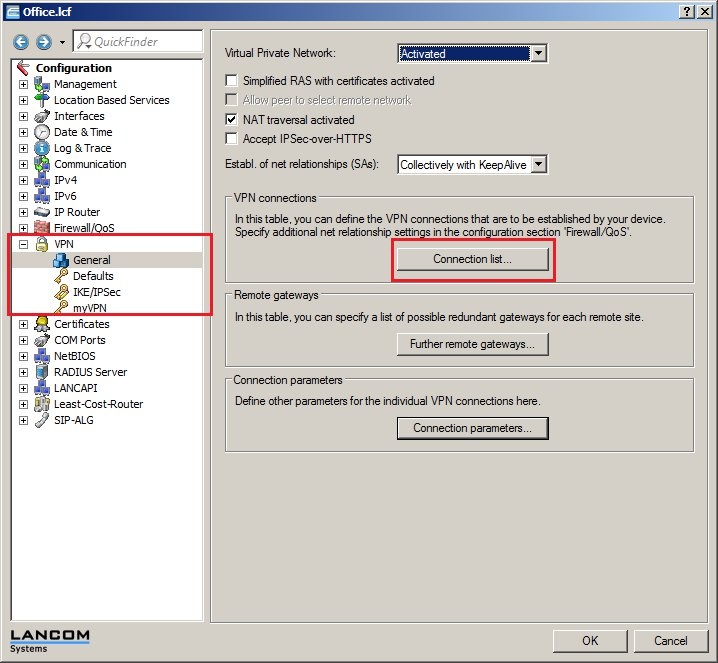
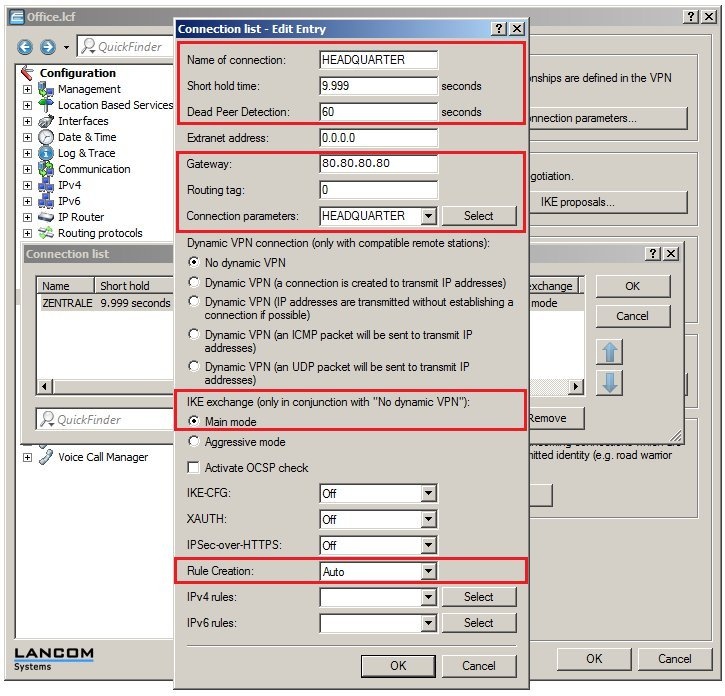
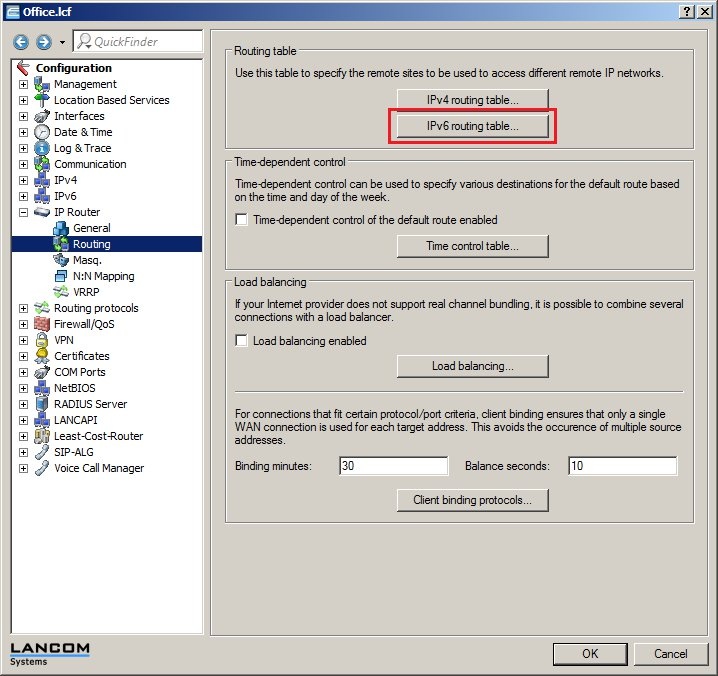
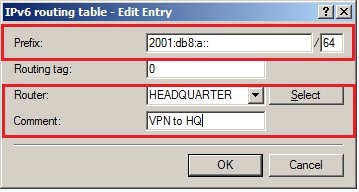
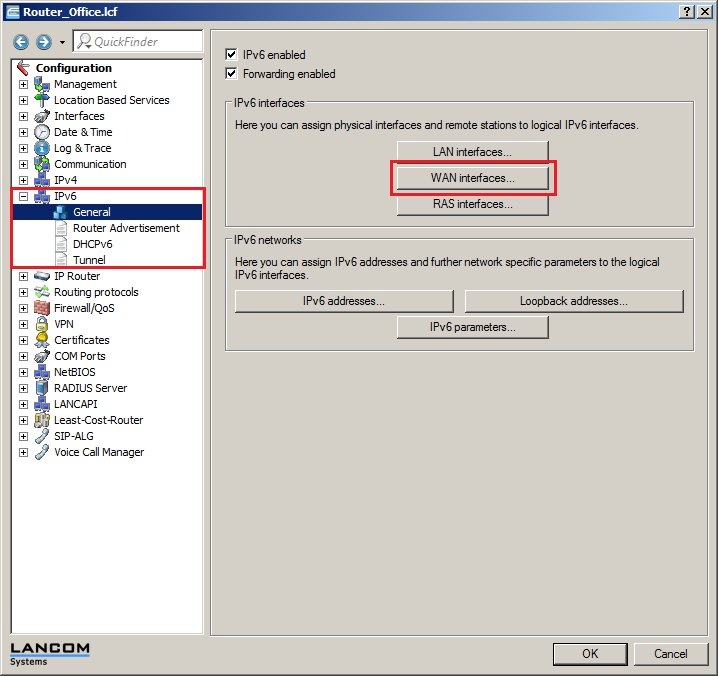
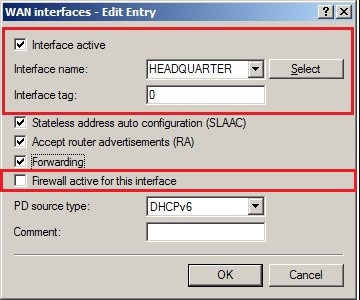
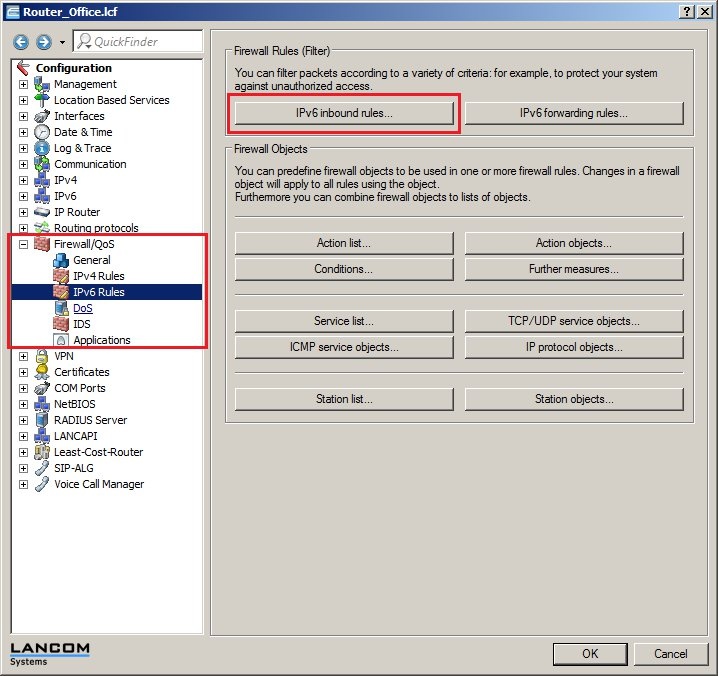
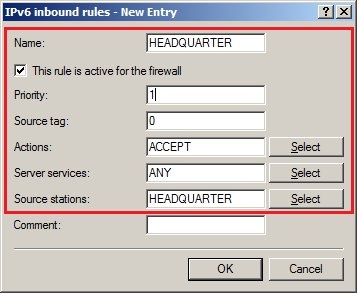
In 2019 the IETF (Internet Engineering Task Force) has designated IKEv1 as deprecated and insecure and therefore it should not be used anymore. LANCOM Systems instead recommends to use the current standard IKEv2. The IKEv1 functionality in LANCOM devices remains intact and can still be used for scenarios where devices without IKEv2 support are used. However LANCOM Systems will not provide any support regarding the troubleshooting of connection problems with IKEv1 connections. Also there won't be any bug fixes or new features for IKEv1. In rare cases a disconnect can occur during rekeying. In such a case it can be useful to increase the lifetimes, so that the disconnects occur less often. |