Description:
This document describes the Rogue AP Detection function of the WLANmonitor program.
Requirements:
WLAN devices that make unauthorized attempts at accessing a WLAN by posing as an access point are called rogues. An example of rogue APs are access points that a company's employees connect to the network without the knowledge or permission of the system administrators, thereby consciously or unconsciously making the network vulnerable to potential attackers via unsecured WLAN access.
Not quite as dangerous, but disruptive all the same are access points that belong to third-party networks yet are within the range of the local WLAN. If such devices also use the same SSID and channel as the local AP (default settings), then local clients could attempt to log on to external networks.
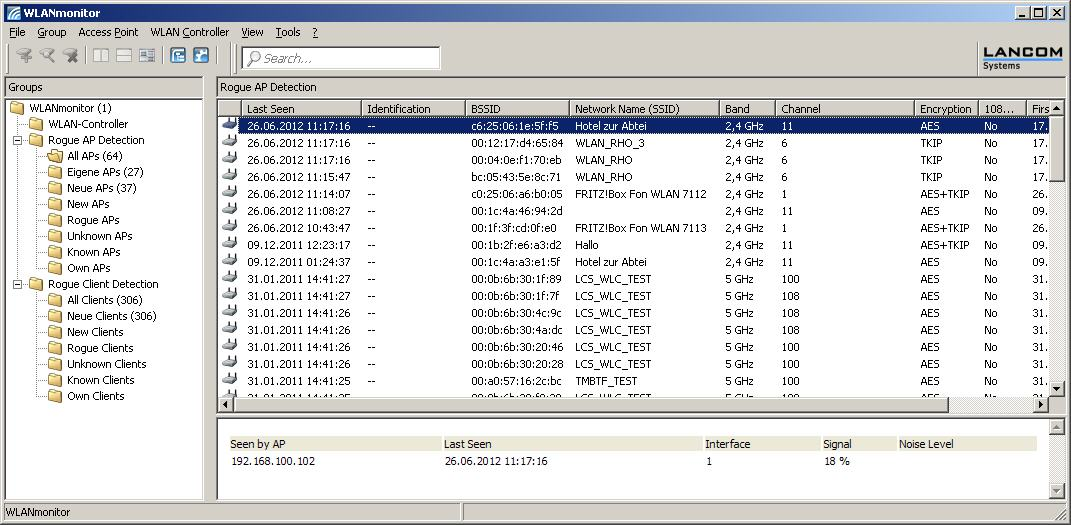
Unidentified access points within the range of the local network frequently pose a possible threat and security gap. At the very least, they are a disturbance. Therefore, WLANmonitor identifies rogue APs and helps to decide whether further measures in securing the local network need to be introduced.
Predefined Groups
All APs: List of all scanned WLAN networks in the following groups
New APs: New unknown and unconfigured WLAN networks are automatically grouped here (APs displayed in yellow)
Rogue APs: WLAN networks identified as rogue and in need of urgent observation (APs displayed in red)
Unknown APs: WLAN networks which are to be further analyzed (APs displayed in gray)
Known APs: WLAN networks which are not a threat (APs displayed in gray)
Own APs: New affiliated WLAN networks from access points monitored by WLAN monitor are automatically grouped here (APs displayed in green)
WLAN networks can be moved to the appropriate groups with the mouse (except for the group 'All APs').
Self-defined sub-groups can be generated under the predefined groups (except for the group 'All APs').
Access points without encryption are also displayed in red.
Detailed information
If you mark a WLAN network with the left mouse button, then further Details are displayed at the bottom of the window:
- The access points which have scanned this WLAN network,
- when the WLAN network was last scanned,
- on which interface the WLAN network was scanned and
- the signal strength with which the WLAN network was received
Background Scan
In order to identify other access points within the device's local radio range, the LANCOM Wireless router can record the beacons received (management frames) and store them in the scan table. Since this recording occurs in the background in addition to the access points' "normal" radio activity, it is called a "background scan".
WLANmonitor surveys the system's own access points. The scan-results tables from these access points are used for rogue AP detection. The background scan is configured in the access point Radio settings.
Important: The background scan must first be configured in the Radio settings of the access points. When configuring the background scan, a time period is defined in which all available WLAN channels are to be scanned once for the receiving beacons. This function is supported as of LCOS 6.20.
WLANmonitor displays the interval for each of the access points being monitored.
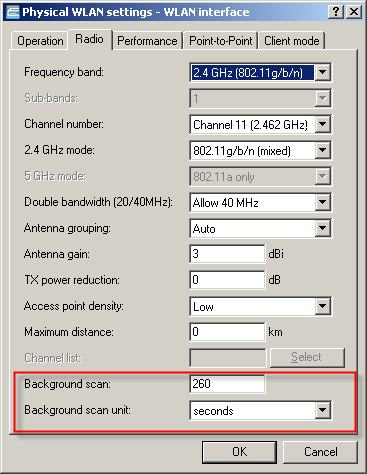
Note on background scan times:
The background scan in the base-station mode detects nearby access points.
The shortest time in the 2.4-GHz band would be 260 seconds. This value causes a further channel to be scanned every 20 seconds (interval/number of channels).
Example:
2.4-GHz band: 13 Channels * 20 sec. = 260 seconds
With the 5-GHz band, which channels are scanned depends on the settings used in the sub-band.
Example:
5-GHz band + sub-band 1+2: 19 Channels * 20 sec. = 380 seconds
Lesser values are not evaluated by the access point, because the smallest evaluable time is 20 seconds per channel.
Higher values result in the later discovery of new neighboring access points, although they increase the available throughput.
Note on the channel list:
This field shows the channels that are searched when automatic channel search is enabled. Invalid channels for the various frequency bands are ignored.
For example, the entry "1, 7-9, 13" means that the automatic channel search is limited to the channels 1, 7 to 9, and 13.
If the channel list contains channels that should be searched, then this applies to the background scan as well. Pay attention to the channels listed here.
Example:
Channels selected by the channel list 1, 7-9, 13
5 Channels * 20 sec. = 100 seconds |
|
|