Description: In scenarios with multiple Internet connections, it may be necessary to route certain traffic over a particular Internet connection. This can be realized with policy-based routing.
However, if the associated Internet connection fails, the data will continue to be routed over a connection that no longer exists. The communication therefore fails.
This document describes how the routing tag of a policy-based routing rule is automatically rewritten to a different route if the associated Internet connection fails, and how to revert to the original tag when the affected Internet connection is established again.
This procedure is suitable for scenarios where a failure of the Internet connection used by policy-based routing prevents communication over the default route with routing tag 0. A typical scenario would feature a load balancer operating more than two Internet connections. In scenarios where the failure of an Internet connection sees the continuation of communication via the routing entry with routing tag 0 (for example, where only two Internet connections are used), an alternative to rewriting the routing tag would be to deactivate the rule and reactivate it again when the connection is re-established. This is described in the following article: 
Requirements:
- Router with at least two configured and functional Internet connections
- Previously configured and functional policy-based routing (see
 )
) - Tool for accessing the router CLI (e.g. PuTTY)
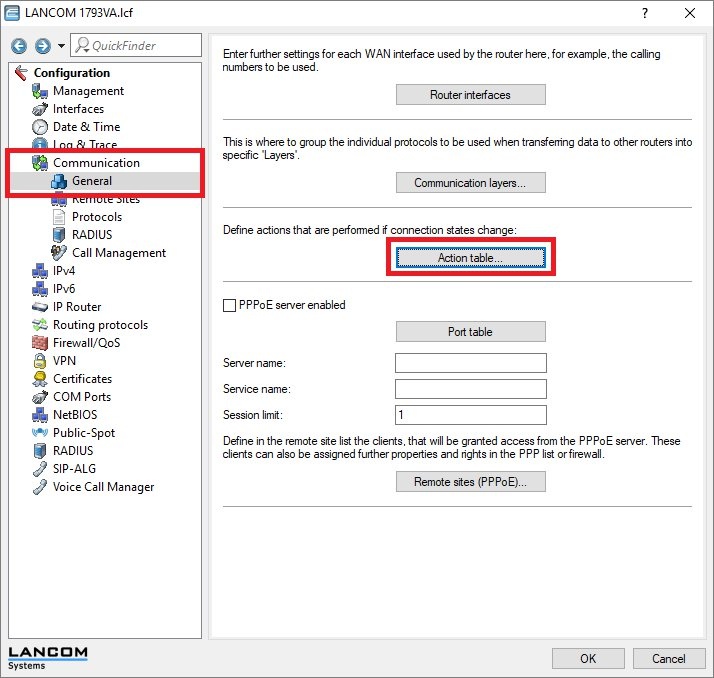
Procedure: 1) Set up the action table to automatically rewrite the routing tag in the policy-based routing rule: 1.1) Open the configuration for the router in LANconfig and switch to the menu item
Communication -> General -> Action table.
 1.2) PPP connection (xDSL):
1.2) PPP connection (xDSL): 1.2.1) Create a new entry and enter the following information so that the
routing tag in the
firewall rule is automatically
rewritten following the
failure of the Internet connection.
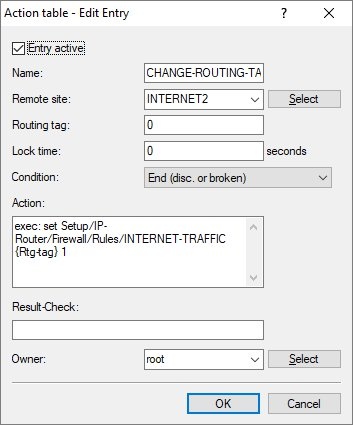
- Name: Enter a descriptive name.
- Remote site: From the drop-down menu, set the Remote site to the Internet connection that the policy-based routing rule uses for routing the traffic.
- Condition: Set the drop-down menu for Condition to End (disc. or broken).
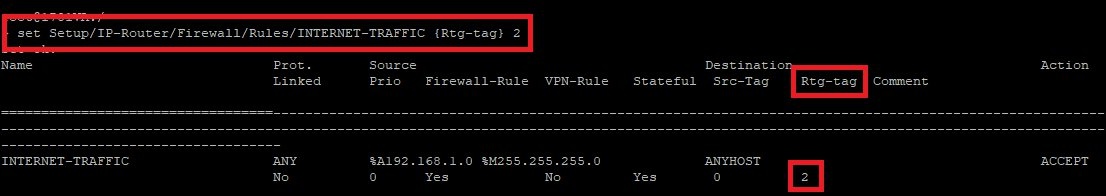
- Action: Enter the following command to assign another routing tag to the firewall rule:
exec: set Setup/IP-Router/Firewall/Rules/<Name of the Firewall rule> {Rtg-tag} <Routing-Tag>
Select the <Routing-Tag> of the Internet connection to be used for communication.
1.2.2) Create another entry and enter the following information so that the
original routing tag in the
firewall rule is automatically specified following the
establishment of the Internet connection.
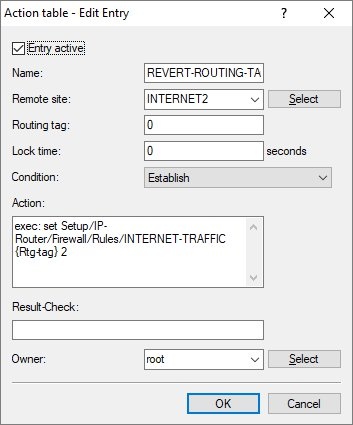
- Name: Enter a descriptive name.
- Remote site: From the drop-down menu, set the Remote site to the Internet connection that the policy-based routing rule originally used for routing the traffic.
- Condition: Set the drop-down menu for Condition to Establish.
- Action: Enter the following command so that the firewall rule reverts to the original routing tag:
exec: set Setup/IP-Router/Firewall/Rules/<Name of the Firewall rule> {Rtg-tag} <Routing-Tag>
Select the <Routing-Tag> of the original Internet connection so that communication is redirected that way.
1.2.3) Write the configuration back to the router.
1.2) IPoE connection (Plain Ethernet): 1.2.1) Create a new entry and enter the following information so that the
routing tag in the
firewall rule is automatically
rewritten following the
failure of the Internet connection.
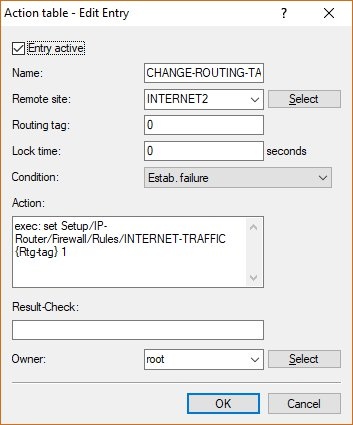
- Name: Enter a descriptive name.
- Remote site: From the drop-down menu, set the Remote site to the Internet connection that the policy-based routing rule uses for routing the traffic.
- Condition: Set the drop-down menu for Condition to Estab. failure.
- Action: Enter the following command to assign another routing tag to the firewall rule:
exec: set Setup/IP-Router/Firewall/Rules/<Name of the Firewall rule> {Rtg-tag} <Routing-Tag>
Select the <Routing-Tag> of the Internet connection to be used for communication.
1.2.2) Create another entry and enter the following information so that the
original routing tag in the
firewall rule is automatically specified following the
establishment of the Internet connection.
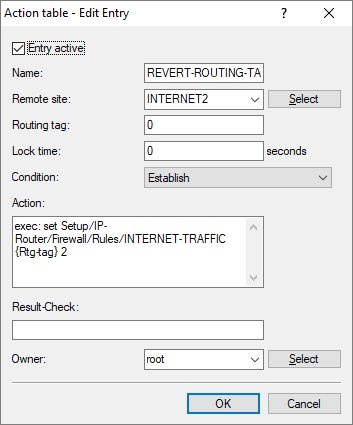
- Name: Enter a descriptive name.
- Remote site: From the drop-down menu, set the Remote site to the Internet connection that the policy-based routing rule originally used for routing the traffic.
- Condition: Set the drop-down menu for Condition to Establish.
- Action: Enter the following command so that the firewall rule reverts to the original routing tag:
exec: set Setup/IP-Router/Firewall/Rules/<Name of the Firewall rule> {Rtg-tag} <Routing-Tag>
Select the <Routing-Tag> of the original Internet connection so that communication is redirected that way.
1.2.3) Write the configuration back to the router.
2) Optional: Testing the commands on the CLI We recommend that you test the functionality of the commands saved in
Step 1.2 in advance.
Important: - From the CLI, the commands are specified without
exec:2.1) Connect to the router’s CLI and enter the following commands.
- Rewrite the routing tag of the firewall rule:
set Setup/IP-Router/Firewall/Rules/<Name of the Firewall rule> {Rtg-tag} <Routing-Tag>
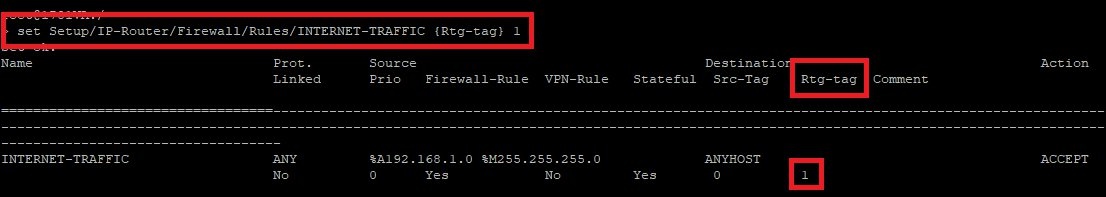
- Reset the routing tag to the original value:
set Setup/IP-Router/Firewall/Rules/<Name of the Firewall rule> {Rtg-tag} <Routing-Tag>